Aadhar: The Impending Risk of Misuse
Okra
Background
In May 1999, the Kargil armed conflict took place between Pakistan and India, at Kargil, along the LOC. In the aftermath of the war, a committee was set up to study the perceived failures of Indian intelligence agencies. Aadhar, stemmed from the recommendation given by this Kargil Review Committee after the Kargil war with Pakistan. A multipurpose singular national identity card was proposed for residents of border states. This was proposed due to forged passports and multiple passports being obtained by individuals perceived to be a threat to the Indian state. The lack of digitisation and synchronisation of records, was also cited as one of the reasons for this. A unified multipurpose identity was proposed to solve this problem. This proposal was further developed by the following UPA regime, which set up the UIDAI, the governing body in charge of dispensing and managing Aadhar.
What Is Aadhar?
Aadhar is the unique identification number proposed and implemented by the Indian government for its citizens. The body in charge of this number, is the UIDAI. Aadhar is basically a unique set of identifiers comprised of demographic data and biometric data pertaining to the individual. These are attached to a unique 12 digit number, called the Aadhar number. The Aadhar number is often printed on a card with a QR code, to make it easier to take avail of facilities using Aadhar.
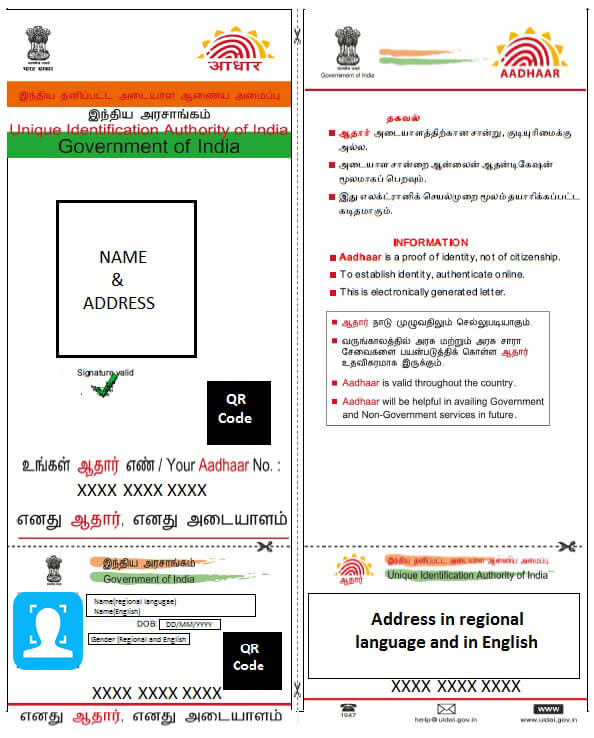
The Aadhar card is used to access government welfare schemes on being linked with the said scheme. These schemes include the old age pension fund, MNREGA(Mahatma Gandhi National Rural Employment Guarantee Act), the public distribution system to name a few. The government has aggressively pushed for compulsoryAadhar use by citizens. To link it not just to government schemes, but to all sectors like banking, healthcare, telecom services etc. By doing so, a single identifier can be used across platforms. he government claims fraud will be reduced and transactions will be streamlined. However, there are many issues with Aadhar such as:
- Whether it is worth the investment
- What about India's poor IT infrastructure that provides little to no security, often ?
- Duplication
- Misuse of data by the State
- Insufficient legal framework
One only needs go through the complaints on the complaint board, to see how individuals have had their lives disrupted by the government pushing for Aadhar and the manner in which it is being implemented.
While most of the criticisms of Aadhar have been around data security and its inefficiency if implemented, almost no discussion has happened around integration of Aadhar into third party platforms. This article will explore the potential misuse by a third party or the state by showing how it's possible.
Third Party Integration
Nandan Nilekani, the co-founder of the IT company Infosys, was appointed as the head of the UIDAI. He resigned in 2014, but has continued to play a key role in convincing the government that Aadhar is a flawless. At the #Future conference, organised by the Kerala government to promote the state among IT companies and entrepreneurs, Nandan Nilekani said Aadhaar is generating data that Indians will be able to sell or barter for benefits. The use of Aadhar as an authenticator on private platforms therefore stands on shaky grounds. Given the recent Cambridge Analytica scandal, it becomes important for us to see what frameworks are in place to ensure the privacy of the individual and prevent misuse. Cambridge Analytica used data obtained via Facebook, to create voter profiles and targeting strategies in the US elections. These profiles would predict the openness, orientation, gender, attitude towards entities etc, to help tailor a targeted message, to achieve the desired behaviour from the said individual. This proved that third parties in hand with political entities gaining access to individual specific data, is a very real threat to democracy.
Skype was one of the first private entities to use Aadhar to authenticate its users identity. How does a private company gain access to Aadhar data and to what extent? The developer edition Aadhar API, costs 5000 inr per month, about 95$ and gives access to Aadhar data. Using the API one can check whether the Aadhar number exists and whether the accompanying data is valid. The government of India is pushing for Aadhar to be linked to mobile numbers, bank accounts, applications, payment portals etc. Doing so holds risks private entities collecting data using unique identifiers and building a profile. These profiles, when collected from across platforms, can build a single unified, and thorough profile of an individual. These profiles could be built keeping in mind elections and marketing – two most widespread instances where individual profiles are built. Also, the more places the data spreads, greater the chance of its leakage.
Both risks are very real, and a short exercise demonstrates both. We tried to gain unique identifiers about individuals via their Aadhar linkage across platforms, and use it to build a profile. No security was breached in this attempt, publicly available records, data and software were used to demonstrate the dangers of linking Aadhar with third party platforms.
i) Obtaining printable Aadhar cards around 3000 documents containing Aadhar card scans, housing plans, fingerprint scans, photographs and stamp papers, were easily obtained by exploring government website architecture and queries. The incessant linking of Aadhar across platforms, made it easier to search for data as well. Once you know that an Aadhar number is used as one of the data points, using it as a search term, also puts the Aadhar holder at risk. One of the sample Aadhar card and fingerprint scans is given here as proof.
ii) Obtaining other such as biometric and demographic details. The source from which the Aadhar cards were obtained also had hundreds of biometric records, photographs, stamp papers etc. One such list of fingerprint scans found can be seen here


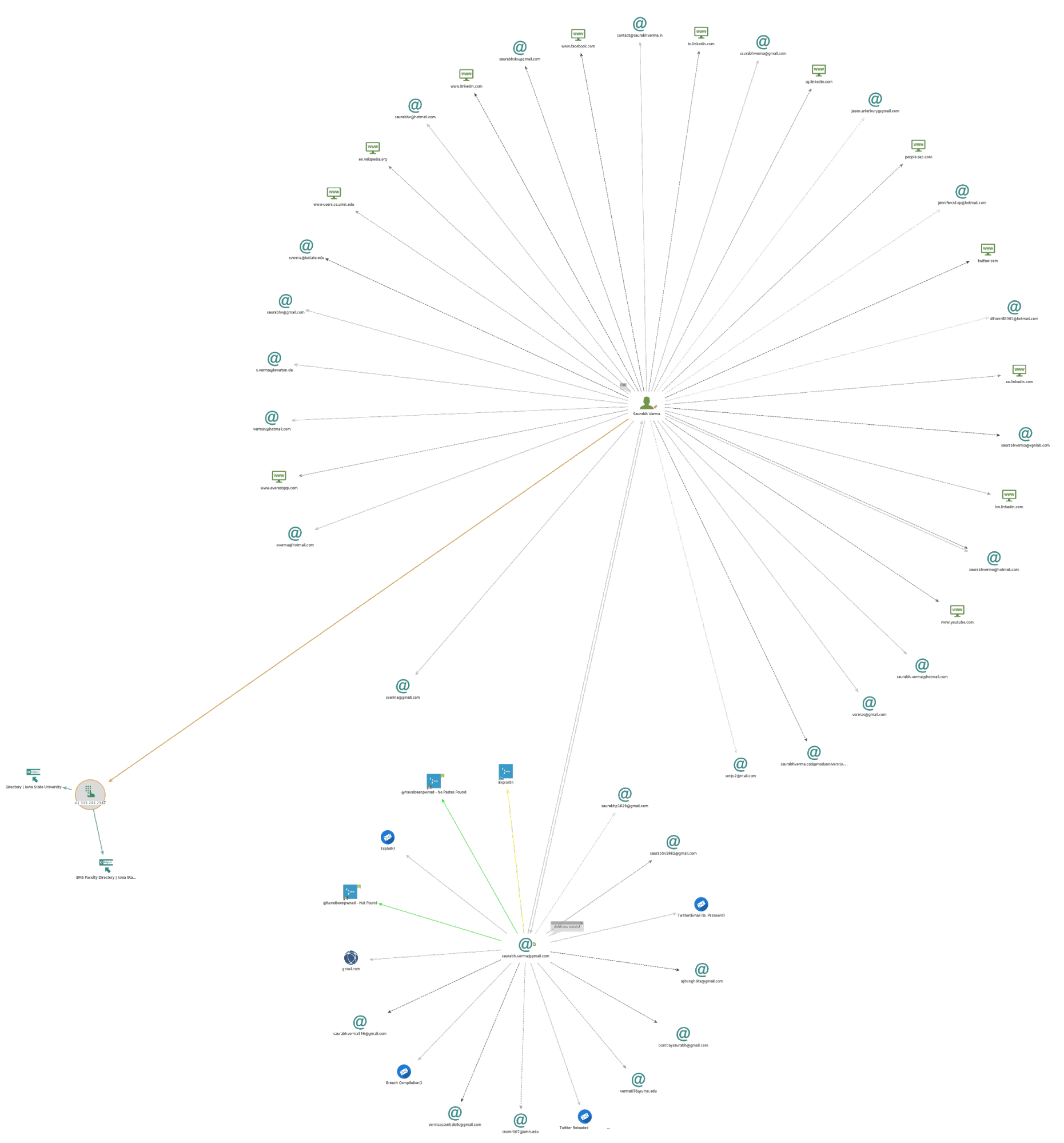
iii) Profile Building: We will try to collect information on this individual, using a profile building tool. Profile building was done using Maltego an information gathering tool. Using the individual's demographic data and biometric data obtained via Aadhar, we can crawl the web to find instances where the individual appears and has been referred to. Digging a bit deeper in the right places, using transforms, provides us with a deeper picture of the individual. It provides us with their Facebook page, their Instagram, any social media they’re on, lists they’re on etc. Maltego provides us with a large list of entities to search for. This is a sample profile, built using transforms applied to just the first level of data. It links the individual to their various online profiles as can be seen here. Once enough profiles are aggregated, then a regression model is run to make predictions about the person. The following image gives an idea of what could be extracted from the data.
A private firm like Cambridge analytica or Palantir could easily build a tool to scrape data across platforms and build a unified voter profile for example. They could identify the conscientiousness of the individual, how open they might be financial incentives, religious incentives, what issues matter to them, who do they follow etc. Palantir in fact already has a tool that is commercially available called Gotham that can be used for such reconnaissance purposes as shown in Palantir's demonstration video here. A lot more can be done using a tool like Gotham compared to a free software like Maltego.
The ruling party, BJP, even revealed that it does use social engineering and targeted political messaging using social media, to sway voters and influence them. Elections in the state of Karnataka happened on May 12th, 2018, and prior to this, the BJP IT Cell co-convenor of Karnataka, has stated on the record that they use 'social engineering' and 'big data analytics' to influence voters. Hashtags were created, and made to trend, in order to influence public opinion. Tailored messaging was created to tell people who have opposing views that 'what you think is wrong, this is what is right and real'.
Given this recent revelation, it is clear the political parties in India are not the most morally upright and they do not shy away from using an individual’s data, to target them and influence them. Therefore, the danger of Aadhar being misused by political parties and third parties, is very real.
Conclusion
This is only the simplest instances where a profile of an individual is built based on data that was readily available. The issue with Aadhar lies deeper in its conception as a unique identifier that can be easily accessed by anyone with the means to and the potential for its misuse.
Aadhar is being passed as a money bill, which means it needn't be approved by the Rajya Sabha(the upper house of the parliament). Currently, the case to decide whether Aadhar violates the right to privacy and is unconstitutional by nature, is ongoing and the judgment has not been given. The current government is the defendant, and is trying to prove Aadhar is not unconstitutional, even though a prior judgment had the bench of 9 judges unanimously agreeing that it was in fact an invasion of privacy. The legal framework has yet to catch up with the times and the authorities turn a blind eye towards evidence against Aadhar. It remains to be seen, what course this takes and whether Aadhar wins over the rights of the citizen. □
Okra is a communications and UX Designer based in New York. He is currently pursuing an MFA in Design and Technology at Parsons School of Design.
