Dark Data in Blockchain Ecosystem
by speculative data
This is a speculative piece on the blockchain ecosystem. I acknowledge the environmental impact that cryptocurrencies currently have. My intent is to focus on blockchain and proceed with faith that blockchain technologies will evolve over time.
Currently, major data generators like TIFAAANG (Twitter, Instagram, Facebook, Apple, Amazon, Alibaba, Netflix, Google) are the biggest dark data holders. Additionally, from local grocery stores, multinational companies, different layers of governments, schools, universities, hospitals, etc., all generate data of different scales and scopes. The global scale of such data could be around 7.5 septillion (7,700,000,000,000,000,000,000) gigabytes per day. Out of which, a tiny fraction could be utilized, and the remaining unused data is dark data.
Collectively, online human behaviours have created massive amounts of activities, fortunes, jobs, opportunities, knowledge, and leisure. Tech companies of all sizes have utilized our online data for their profit maximizing activities.
Numbers are the crystal ball in the modern world. Companies are monetizing massive amounts of data to advertise, connect, and share. In fact, new businesses are emerging to collect data and sell to bigger companies. Utilizing other forms of technology, businesses are being built using Artificial Intelligence to help other businesses share and analyze data securely. Hence, data has value and businesses of any size will gladly agree — the more data they have, the more they will utilize them for their benefits. Even USPS is monitoring your social media posts.
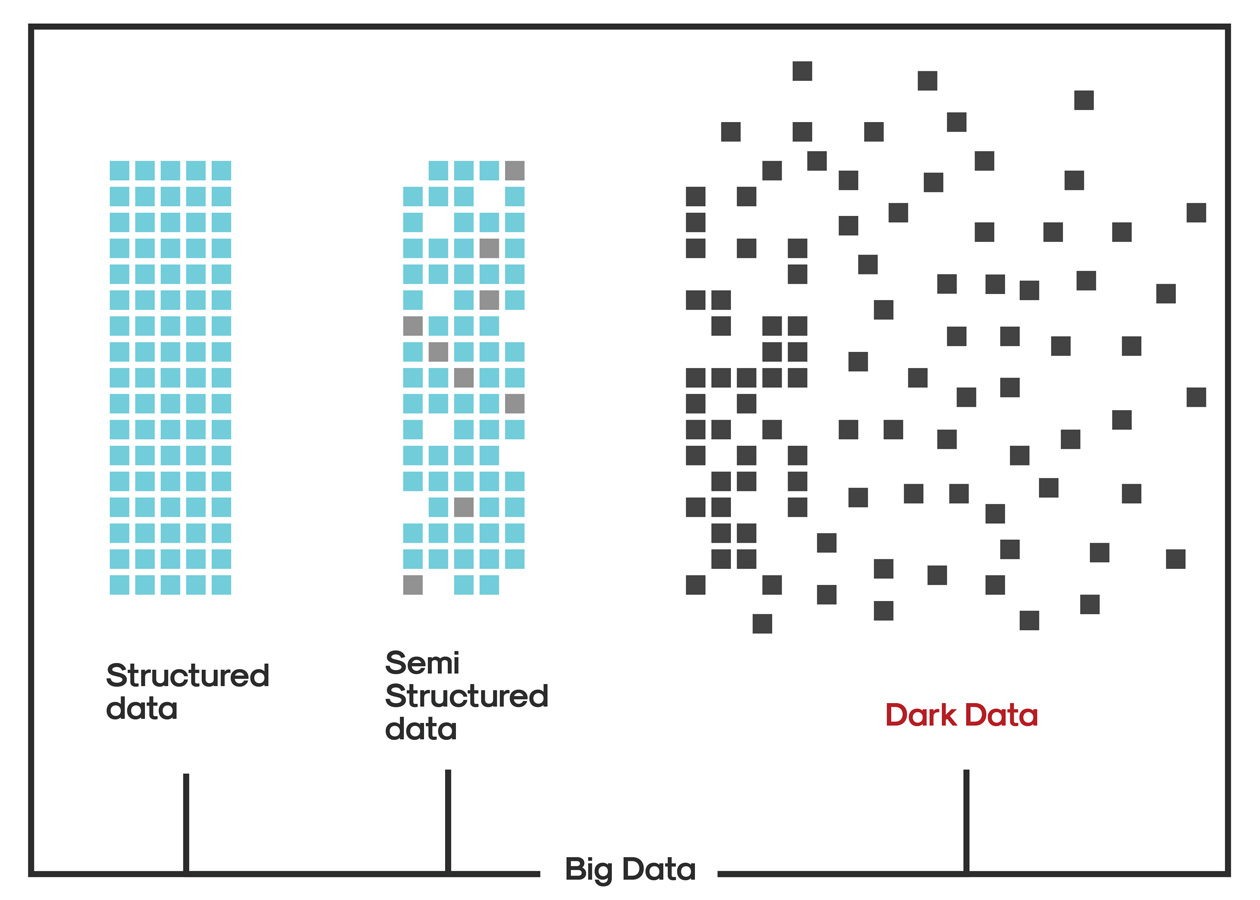
Dark Data is a mixture of raw and processed data that organizations/agencies collect and store. You may have heard of big data, which is massive amounts of information. Inside that large data set, only just a portion of that data set is going to be structured and used, such as: age, name, location, and phone number. Semi-structured data is loosely organized data, such as: tweets organized by hashtags, emails by inbox, etc. The remaining data, unstructured data, also known as Dark Data by the IT industry, signify information warehousing that is not organized in a clearly defined framework or model, such as sounds, digital surveillance photos, and sensor data. Dark data has the potential value for any business because there may lie unfiltered information, which can be used as a monetization method, if utilized properly.
A leading global consulting firm, Deloitte, states:
“There are different types of dark data. Take a message, such as a tweet. A tweet is ‘dark’ as it needs to have the language extracted so that a computer can analyse what is written in it. The metadata around the tweet is ‘dark’ also - the time of day sent, the @user, the #hashtag, the device, the location. Analysing the text in the tweet gives you an insight into what is being said, who said it, how happy or angry the sender is. The tweet may contain images or audio, which when analysed using image recognition tools can extract content such as descriptions or terms…”
So a tweet is not just a tweet, it can be of value depending on who wants it and how they plan on using it.
I believe that Dark Data right now, is waiting for something. While it may or may not be used by organizations, it is something that should not be ignored. Dark Data is waiting for a technology to take it to the next level, to add value or exploit for profit to cause untaxed externalities. I believe blockchain is technology that has the potential to add value as well as to secure such data with proper ownership. In simple terms, blockchain is a decentralized distributed database system without any need to trust central parties.
Trust is something that the Cypherpunks did not have for the central banks and their control over monetary policy. The Cypherpunks are an eclectic crew of hackers, hobbyists, technologists, and rebels sharing a core belief “that the internet would soon become an important battleground for human freedom”. They were right on their suspicions with the 2008 market crash. In 2008, central banks (government) spent massive amounts of money to bail out failing banks for frauding the American People.
To curious readers that wish to know more about The Cypherpunk movement, a book Digital Cash: The Unknown History of the Anarchists, Utopians, and Technologists Who Created Cryptocurrency by Finn Brunton is a good source of information. The NYU Professor Finn tells the story of the pioneers of cryptocurrency, cryptography, the technical experiments, encryption, attempts, and failures to create the first digital currency and the technologies involved. Digital Cash also explores the wider questions of what makes digital objects valuable, and how do we learn to trust and use different technologies along the way? Another resource to learn more is this FAQ called: THE CYPHERNOMICON.
Which brings us to the creation of Bitcoin, by an anonymous group or individual that goes by Satoshi Nakamoto. Bitcoin was created amidst the 2008 market crash and has been the topic of many controversies. However, it wasn’t just “Bitcoin” that was revolutionary, but it was what was inside. What was this significant intangible, unknown complex technology inside Bitcoin in 2009? Blockchain. Big banks are profiting fortunes using data, however they failed to understand cryptocurrency and blockchain, and flatly dismissed their existence for years.
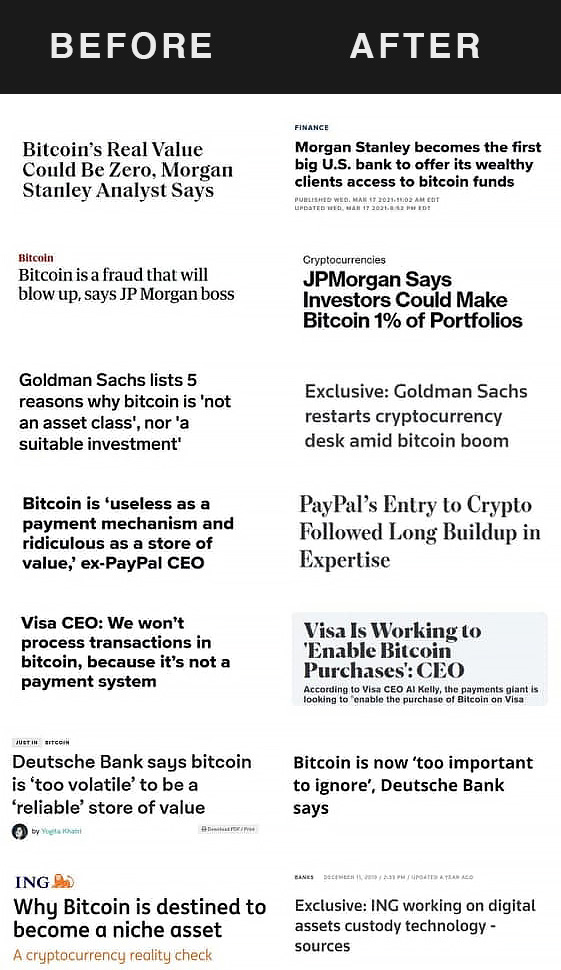
Until some interns presented the various use cases of Blockchain, why cryptocurrencies are here to stay, even the CIA is onboard and probably added in an explainer video. Although, one has to wonder if the dynamics going on in workplaces about technologies are akin to Dilbert’s workplaces…

Why Blockchain and what is it?
Investopedia defines blockchain as:
“One key difference between a typical database and a blockchain is the way the data is structured. A blockchain collects information together in groups, also known as blocks, that hold sets of information.
Blockchain is essentially a decentralized ledger that does not need a central authority or a 3rd party affiliate to control. It does not require a central entity because certain blockchains require a Proof-of-Work (PoW) algorithm. PoW is a mechanism that allows the decentralized network to come into agreement for any transactions. However, proof-of-work (also known as crypto-mining) has severe environmental impact due to its electricity usage to solve the algorithms. There could be millions of miners around the world and that magnifies the overall environmental impact.
The original blockchain was created inside Bitcoin. However, in the past decade there has been a rise of more advanced blockchains such as Ethereum. The early creators of Ethereum also realized the potential of blockchain and some began diving into other blockchain-related projects as well. Dr. Gavin Wood left Ethereum and pursued creating another blockchain called Polkadot. Dr. Gavin Wood is a computer programmer, co-founder of Ethereum, and inventor of Solidity, the computer programming language used in the Ethereum Blockchain. Currently, Ethereum blockchain is using the Proof-of-Work protocol, and Polkadot is using the Proof-of-Stake (PoS). Proof-of-Stake uses an election process to validate blocks, and provides an alternative to the heavy computational power of proof-of-work consensus algorithms.
There are many ongoing developments and research surrounding blockchain since its creation in 2009. In the United States, a crucial framework was published in October of 2020, Attorney General William P. Barr announced the release of “Cryptocurrency: An Enforcement Framework,” a publication produced by the Attorney General’s Cyber-Digital Task Force. The 80+ page document published by the DOJ (Department of Justice), is significant in a few different ways. One, by even releasing a framework, it shows to America and the world that the DOJ is focusing on crypto. Two, as Coindesk indicates,“the document also suggested the U.S. government would enforce its laws regardless of where exchanges – referred to as virtual asset service providers, or VASPs – are based. In other words, these exchanges should comply with U.S. laws – even for their non-U.S. customers”. Three, there’s a section (page 20, II. Law and Regulations) in the framework that lists all of the laws that the DOJ can use to counter malicious activities. A stepping stone in the right direction, due to so many cryptocurrency-exchange platforms emerging and various use-cases of cryptocurrencies evolving.
Another hurdle that Blockchain has to go through is the image problem. Cryptocurrencies are notorious for bad actors such as scammers and hackers. It seems almost every month there is a new crypto-scam/pyramid scheme appearing, however it is important to clarify that implementing blockchain for business purposes is not the same as hyping and marketing cryptocurrencies. Blockchains serve as an infrastructure to create cryptocurrencies, without blockchains there are no cryptocurrencies.
Koray Caliskan, author of “Data Money: The socio-technical infrastructure of cryptocurrency Blockchains” defines cryptocurrency as “data money.” Blockchain allows the rights to move data in the digital space. The paper describes a blockchain as a digital actor-network platform that makes it possible to define and distribute these data transfer rights.
Why Blockchain: My proposed concept of developing blockchain as the infrastructure for a permanent data lockbox for all dark data. It will be a technological base to resolve the issue of privacy paradox. For example, Professor Vincent Mitchell and Bernadette Kamleitner argue “ One way to increase the sense of ownership would be to create a system where individuals are able to sell their personal data or, as has been promoted by California governor Gavin Newsom, to institute a ‘data dividend’ whereby some percentage of the revenue generated from users’ personal data is returned to the user.” Therefore, blockchain can be a potential for an alternative direction for combating data rights.
Some of the newly proposed New York Privacy Bills, require businesses to act as “Data Fiduciaries.” New York State Senator Kevin Thomas stated, “Fiduciaries, like an attorney or a doctor hold onto your information. They don’t share it, unless there is a need for the purpose for which they collected it. That’s not what’s going on here with these data companies, and these data brokers. They’re sharing it and we’re getting targeted.” However, one of the main problems emerging from these kinds of laws is hindering other state’s rules and regulations.
Lina Khan has argued that the proposed NY bill is incompatible with existing law in Delaware, where many of the tech giants are incorporated, that requires companies to maximize returns for shareholders. This causes the interests of stockholders and users to diverge. Directors of companies may be put in unforgivable positions of having to violate their fiduciary duties to stockholders under Delaware law, in order to fulfill their fiduciary duties to New York users. This is just for New York State, and there are many other states that are proposing slightly different bills. At this rate, more complexities for businesses and the general public are bound to rise and in an effort at simplification, may lead to Federal legislation that might be more palatable to lobbyists, but offer less protection to citizens.
However, the question remains on who should have ownership of an individual’s data: people, businesses, or government? In absence of data regulation and data protection, how can technology be the bridge for all stakeholders?
Conclusion
Individual concerns on dark data will increase in coming days and years. Dark data accumulation will multiply as well. A few state governments such as New York and California are trying to address the data privacy and rights. But, how the government is going to govern big data issues along with the individual’s rights to have ownership and manage their personal data is in the dark because of lack of proper rules. Additionally there is a lack of internationally accepted data governing framework. New startups attempting to tackle dark data may not be effective due to non-existing regulations.
Blockchain ecosystems could be the viable technological intervention in order to protect people’s privacy and data rights. This sort of new technology could be developed in public- private collaboration in order to manage dark data. For example, major data generating activities of TIFAAANG (Twitter, Instagram, Facebook, Apple, Amazon, Alibaba, Netflix, Google) and other corporations can use “blockchain ecosystems’’ to keep individuals’ data secured and compensated. Meanwhile, the government could (and should) introduce new rules for blockchain data management and privacy, because the technology has the potential to bridge the trust among all players in the ecosystem: government, businesses and people.
speculative data is a collection of user data generated from a location within the crop circles. They are not a tool of A.I but rather an agency of A.T (Alien Technology).
Sources:
- https://www.cnbc.com/2021/03/30/new-york-state-senate-passes-bill-to-legalize-recreational-weed.html#:~:text=Key%20Points-,Gov.,the%20drug%20for%20recreational%20use
- https://www.coindesk.com/price/dogecoin
- https://www.forbes.com/advisor/investing/what-is-dogecoin/
- https://www.brides.com/does-online-dating-work-5112033#:~:text=The%20Research,something%20casual%20or%20long%2Dterm.
- https://www.businessnewsdaily.com/10625-businesses-collecting-data.html
- https://www.eu-startups.com/2020/08/berlin-based-apheris-raises-e2-5-million-to-help-companies-share-and-analyse-data-securely/
- https://www.vice.com/en/article/pkd7pk/banjo-ai-surveillance-utah-contract
- https://www.datamation.com/big-data/structured-vs-unstructured-data/
- https://news.yahoo.com/the-postal-service-is-running-a-running-a-covert-operations-program-that-monitors-americans-social-media-posts-160022919.html
- https://www2.deloitte.com/ch/en/pages/innovation/articles/dark-data.html
- https://nakamoto.com/the-cypherpunks/
- https://www.amazon.com/Digital-Cash-Anarchists-Technologists-Cryptocurrency-ebook/dp/B07MDHTPB9
- https://www.forbes.com/sites/mikecollins/2015/07/14/the-big-bank-bailout/?sh=69fca00e2d83
- https://www.reddit.com/r/Bitcoin/comments/ma5lmd/bitcoin_before_and_after_headlines/
- https://www.cbinsights.com/research/industries-disrupted-blockchain/
- https://www.fnlondon.com/articles/weve-crossed-a-line-why-goldman-sachs-says-crypto-is-here-to-stay-20210316
- https://decrypt.co/66411/cia-bitcoin-surveillance
- Blockchain Expert Explains Blockchain https://www.youtube.com/watch?v=hYip_Vuv8J0
- https://www.investopedia.com/terms/b/blockchain.asp
- https://www.coinbase.com/learn/market-updates/deep-dive-ethereum-economy
- https://polkadot.network/what-is-polkadot-a-brief-introduction/
- https://www.justice.gov/opa/pr/attorney-general-william-p-barr-announces-publication-cryptocurrency-enforcement-framework
- https://www.finextra.com/blogposting/18496/remaining-challenges-of-blockchain-adoption-and-possible-solutions
- https://www.justice.gov/opa/pr/attorney-general-william-p-barr-announces-publication-cryptocurrency-enforcement-framework
- https://www.newyorker.com/magazine/2021/04/26/the-incredible-rise-of-north-koreas-hacking-army&sa=D&source=editors&ust=1619454734060000&usg=AOvVaw1GiwOipXl2PF6dOM8gCZ8d
- https://hbr.org/2017/01/the-truth-about-blockchain
- https://reallifemag.com/money-for-nothing/
- https://www.tandfonline.com/doi/abs/10.1080/03085147.2020.1774258#:~:text=Data%20money%3A%20The%20socio%2Dtechnical%20infrastructure%20of%20cryptocurrency%20blockchains,-Full%20Article&text=Drawing%20on%20an%20empirical%20study,based%20taxonomy%20of%20cryptocurrency%20blockchains.
- https://www.nysenate.gov/newsroom/in-the-news/kevin-thomas/new-yorks-privacy-bill-even-bolder-californias
- https://www.wired.com/story/new-york-privacy-act-bolder/
- https://www.youtube.com/watch?v=7jY_ZP6gQiQ
- Goo goo Dolls - Slide https://www.youtube.com/watch?v=yP4qdefD2To
- https://themarkup.org/privacy/2021/04/15/big-tech-is-pushing-states-to-pass-privacy-laws-and-yes-you-should-be-suspicious
- https://originstamp.com/blog/top-blockchain-startups-to-watch/
- https://venturebeat.com/2021/04/21/blockchain-startup-digital-asset-nabs-120m-to-knock-down-data-silos/
- What is the difference between Bitcoin and blockchain? Youtube: <https://www.youtube.com/watch?v=MKwa-BqnJDg
- https://www.washingtonpost.com/business/2021/04/16/half-countrys-remaining-mall-based-department-stores-are-expected-shutter-by-2025/
- https://www.nbcnews.com/business/business-news/amazon-snapping-disused-shopping-malls-turning-them-fulfillment-centers-n1262914
- https://www.wsj.com/articles/malls-fill-vacant-stores-with-server-rooms-1415042980
- https://www.ft.com/content/cfe4ca11-139a-4d4e-8a65-b3be3a0166be
- https://www.foreignaffairs.com/articles/united-states/2021-04-16/data-power-new-rules-digital-age