Why I am crocheting my data and you should too
by Michelle Nee
For years there has been a Google Drive folder nestled among my work and school documents titled, “personal”. True to its name, the folder contained all of my personal information I needed (or was told I needed) for things like registration, applications, purchases, and even a text file of all my Google searches. Then I received a “CRITICAL ALERT” email. My information was part of a data breach.
We often look at our personal computer as a hub of it all. The entirety of my identity has rested among text files and photos for years. Crucial information that I am too worried about having in a drawer, where someone else could find it, was put onto my Google drive. I grew up alongside the growing opacity within the Technology industry. It was easy to rest on the laurels of large tech companies’ credentials. But after the breach, I had to begin asking myself if the same tool I use to make myself known to the digital world and connect with others is the same tool I should use to store my personal data. After having my data leak as a part of a large Google data breach, I downloaded my data from Google using Takeout and sat face to face with the fact that I was the last person to get my hands on this information. Encryption became a (somewhat necessary) fascination for me. For years my fear had been hackers getting hold of my information. Now, my fear became not having control of my personal data. If by placing my data in cyberspace I am left vulnerable, why not store it by non-digital means?
Having physical data is not a groundbreaking idea by any means. In World War 2 spies would knit messages in a code to send back from behind enemy lines. This practice was mainly done by resistance fighters in Belgium during World War 2 but it is not the only time that craft encryption has been used. Female spies during the Revolutionary war would knit messages from behind british lines.1 During slavery freed slaves would create encoded maps on quilts to help other victims escape trafficking. In the province of Hunan women created a language known as Nüshuas a way to cope with the exclusion from hanzi writing, due to the fact they were women and not men.2 Women would embroider the characters hiding them in ornate or simple works. Oftentimes this practice is harnessed during resistance movements as the dynamic is often the hyper visible utilizing inconspicuous practices against surveillance of a large body and sometimes, such as in the case of spies employing this tactic, turning the eye back onto the surveilling power. Encrypting data using craft is not just a security measure but it also follows a long line of resistance and countering power imbalance.
Where a computer encrypts data using a cipher, the same can be done to store physical data by creating a crochet pattern that ‘encrypts’ data by converting it into a data visualization with a color and pattern key; or in the case of Belgian resistance members, knitting morse code into a sweater.3 Using this technique to store data means no third party has access to my data as no one has access to my home. The laws are lagging behind in regards to personal privacy and data protection.
After receiving my information back from google, I sat down and laid out all of the yarn I own. I assigned each color a number and created a sequence of colors and stitches for each letter of the alphabet. This was and still is my cypher. And then I began to physically encrypt all my data. A scarf with my date of birth. Gloves with yearly salary, 2019 on the right hand, 2020 on the left. I even made socks for my most used password. To use the vast majority of the internet there is a sacrifice of privacy, whether or not that sacrifice is known. The days I go to a pair of socks for my social security number as opposed to a photo saved in my “Personal” file are now my favorite.
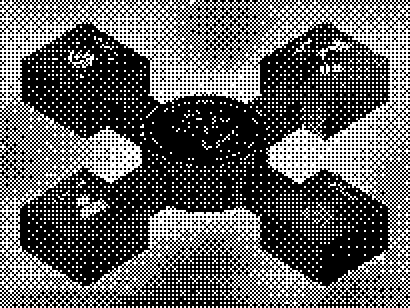
Tracking data using a non-digital means has become a meditative act for me. I have developed both color coded and my own personal code consisting of a combination of specific stitches for each character. Developing a personal cipher is made easier by the precedents of code craft. While I use a combination of stitch sequences for my cipher the knitters of WW2 often used the knit and pearl to hide morse code in. With such a simple act, data is protected better than any security software. Each day I sit down and think about how I will encrypt my data as well as create a physical object to bring me comfort along with the peace of mind. I am suddenly aware of the true depth of my data when I look at the pile of crocheted information becoming larger and larger. The same data that has been collected ,willingly or unwillingly, for most of my developmental years. The first piece I crocheted was a doily containing my date of birth. I really enjoyed it. This practice is easy to pick up and recommended. Anyone can pick up a crochet hook, or knitting needle and create a cipher of their own. This personal cipher replaces the power back into the hands of the person not the corporation. Below, is my date of birth doily to exemplify just one of the possibilities for secure data storage.



Sources:
- Monteiro, Stephen. The Fabric of Interface: Mobile Media, Design, and Gender. Cambridge, MA: The MIT Press, 2017.
- Wu, Amy Suo, and Clementine Edwards. A Cookbook of Invisible Writing. Eindhoven: Onomatopee, 2019.
- Zarrelli, Natalie. “The Wartime Spies Who USED Knitting as an Espionage Tool,” April 15, 2021. https://www.atlasobscura.com/articles/knitting-spies-wwi-wwii.
-
Natalie Zarrelli, “The Wartime Spies Who USED Knitting as an Espionage Tool,” April 15, 2021, https://www.atlasobscura.com/articles/knitting-spies-wwi-wwii. ↩
-
Amy Suo Wu and Clementine Edwards, A Cookbook of Invisible Writing (Eindhoven: Onomatopee, 2019). ↩
-
Stephen Monteiro, The Fabric of Interface: Mobile Media, Design, and Gender (Cambridge, MA: The MIT Press, 2017). ↩